Skip to main content
Anonymous DCOM Problems with remote Hyper V Manager(Access Denied. Unable to Establish Communication)
Running nismap.exe with –y parameter creates a map with "." instead of "_"
"nismap.exe" does not create the map name as expected when using the –y parameter. Below is an example of the attempt to use nismap.exe with –y to create the map named auto_home_svr_test:
C:\temp>nismap.exe
create -i 1 -g " " -s localhost -f
"C:\Windows\IDMU\nis\nis2ad.log" -y auto_home_svr_test
Activity =
Creating map = 'auto.home_svr_test'...
SUCCESS
Creating
With further research, it was confirmed that this is a default behaviour of the nismap function.
Secondary GID not working with ADlookup
Recently we had a case where users from Windows 7, NFS client were unable to access the NFS share. Adlookup was set up properly. And changing the setting to fetch the information from Windows 2003, User name mapping server resolved the issue.
Note: We did not change any settings on the Unix NFS server
Current set up:
- User name mapping configured on Windows 2003
- NFS server configured on Windows 7/ windows 2008 R2/Windows 2003
- AD configured and user's UIDNumber and GIDnumber populated.
- On Unix the parent NFS share is own by user A and group A (permission 770)
- Inside the parent NFS share, subfolders have user and group specific permission.
- Windows user is not mapped to user A and group A but is mapped to the users who has full permission on the subfolder.
While troubleshooting we found that the windows user was getting access to the NFS share through secondary group membership, while using
User name mapping. But the same was not happening with ADlookup.
User name mapping feature was based more on Unix style and it allowed the NFS client to pass the auxiliary GID (secondary group) information to the NFS server. Hence when we are using User name mapping (which is fetching the information from NIS); we pass on the secondary group information. So, though the user A's primary group is X but still the user is able to get the access to the NFS share, since he is also a member of group Y.
On Windows 7\2008 R2, we have an option to fetch the mapping information from Windows 2003 (running user name mapping) and make this work.
But while using ADlookup, it will not pass the secondary group information to the NFS server and hence the access fails for a folder
which has permission '770'.
Suggested options given in this scenario for ADlookup:
In case of ADlookup, we need to add the RX permission for others on the parent NFS share and give the appropriate permission on the sub
folder.
"Server for NFS" service exhibits different behaviour when restarted using different options
While working on a issue recently, we found that there was a difference in behaviour when we restart the "Server for NFS" service from the services console compare to restarting it using the "nfsadmin" command. The issue was happening after a disk was reformatted and could be reproduce if the Service was started from the services console. While if we start the service from the 'nfsadmin' command, the issue cannot be reproduced.
Actually there are two pieces in the "server for NFS" architecture – the user mode service and the kernel mode driver. When we restart the services from the services console only one of the services gets restarted. When we use nfsadmin, it stops/starts both the kernel mode driver and user mode service. This is what is causing the difference.
You can also achieve the same by individually stopping the user mode service and driver using the net command instead of nfsadmin. You would need to run the command below:
- net stop nfsservice
- net stop nfsserver
When starting, you can just start nfsservice which automatically starts nfsserver.
Server for NFS (Windows 2008 R2) crashes as soon as the Clients mounts the NFS share
Recently we got an issue where the NFS server ( Windows 2008 R2 was hosting the NFS share) use to bugcheck as soon as the ESX client was mounting the share.
We found that the size of the NFS share was approximately 189 GB in size. The share was open to everyone and also was the only NFS export on the machine. Also the NFS and RPC drivers were updated as per the KB articles below:
· https://support.microsoft.com/kb/2485543
· https://support.microsoft.com/kb/2662672
We analyzed the dumps and found that the issue is due to the fact the NFS share is already mounted on another client. Ideally, when a share is mounted, on the server , we read the monitor file and notify the client holding locks. When the share is mounted for the first time, the monitor file will be empty. But in this case, it is not. We could see that the ._nfs\monitor got corrupted.
After some more probing we found that this system was running W2K3R2 earlier and the same volume was used to export NFS shares then as well. So it seems there is some problem related to memory/buffer allocations in the routine that reads/updates the monitor file.
Renaming the ._nfs on the volume in question resolved the issue and the bugcheck stopped.
Server for NIS service crashing at the startup
We recently got an issue where the Server for NIS service was crashing at a startup. In the environment, customer had added W2K8 R2 based DC and installed IDMU in his existing W2K3R2 based IDMU setup.
To begin with we tried checking if the numbers of available port are getting exhausted but that was not the issue. Then, took LDIF exports of NIS map for users and group and looked into it. Nothing seems to be wrong from the LDIF exports.
So to further troubleshoot on this, we collected the dumps while the Service was crashing. From the dumps it seemed that the issue was caused because of heap corruption. The dumps were also pointing to one of the user account which may be causing it.
So, we removed the Unix related attributed for this one user and Server for NIS service seems to be working fine. After collecting the LDIF output for this user again we noticed that the unixUserPassword holds two different values for this user.
To summarize the root casue: "A user in the AD was somehow populated with two different values for the unixUserPassword attribute which was causing heap corruption in the NIS service."
To resolve the issue" We removed the unwanted (default) value from the attribute and started Server for NIS.
Setgid/Setuid does not work against a NFS share hosted on Windows 2012
One of our customer recently reported issue where setgid/setuid was not working against a NFS share hosted on Windows 2012. Below are two images which shows the expected behaviour while SGID is set on a local share v/s the unexpected behaviour over a NFS share.
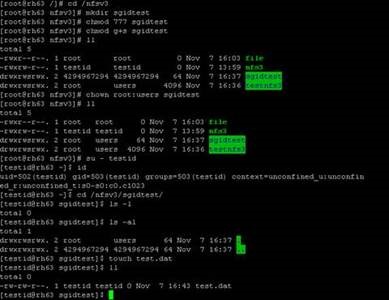 ==> NFS Share
==> NFS Share
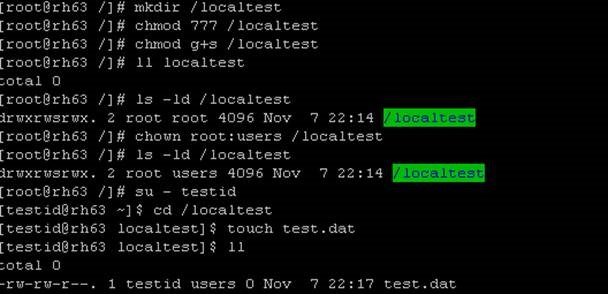 ==> Local share
==> Local share
Through our investigation we could see that the behaviour with the setgid which is been observed is by design and in compliance with the NFS protocol. This is same for Microsoft Windows NFS Server (both v3 and v4.1). Per Windows NFS Server's design, newly created files will always be owned by the user/group that issued the CREATE request; in particular, it does not the owner, group, or mode bits of the parent directory into consideration creating the ACL for the newly created file, nor does the NFS specification require NFS servers to do so. There is an KB article https://support.microsoft.com/kb/951716
Inputs on the SafeSetUidGidBits registry:
The article https://technet.microsoft.com/en-us/library/cc731734.aspx talks about a registry key HKEY_Local_Machine\System\CurrentControlSet\Services\NfsSvr\Parameters\SafeSetUidGidBits = (DWORD)
The SafeSetUidGidBits controls whether the NFS Server will filter out the SetUID/SetGID bits from executable non-directory files when everybody or the file's group is granted write access to the file.
If a file is writable by somebody other than the file's owner, then somebody can replace the file with different contents.
If the file is executable by somebody other than the file's owner and the file has the SetUID bit set, executing the modified file contents will potentially execute the modified file with alternate user credentials, resulting as a potential elevation of privilege vulnerability.
As such, when SafeSetUidGidBits is enabled (the default), then NFS server will tell the NFS clients that the SetUID/SetGID mode bits aren't set so that any client executing the program will execute with the user's credentials rather than alternate credentials.
SUA-SDK, CSH crashes on Citrix XenApp system
We have got many issues reported for SUA SDK, where the korn/ C shell crashes.
While the C shell crashes just after launching the korn shell crashes as soon we run command like clear.
With further investigation, we had found that generally this is because of some anti-virus or Citrix software which inject some code into every process during start-up assuming them to be proper Win32 process. SUA processes we know behave a little different than other Windows processes especially during start up so this looks to be a feasible possibility.
Uninstalling XenApp citrix application does resolves the issue but this was not feasible solution on most of the scenarios.
Hence with further troubleshooting / research and investigation we noticed that there were two citrix drivers were interfering with SUA: rskcore.sys and ctxpidmn.sys
From the crash dumps we could see ctxpidmn.dll queuing which was coming from ctxpidmn.sys (Citrix driver pool allocation). To fix ctxpidmn.sys, follow the steps as per https://support.citrix.com/article/CTX132820
Run regedit.
Add following registry key.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\ctxpidmn
Type: String
Name: UviProcessExcludes
Value: csh ==>For C shell
Separate with colon if necessary for other commands. e.g.) vi;csh;yacc;clear
Reboot server to enable the setting.
Rskcore.sys, is a core part of Citrix Edgesight which is a monitoring agent for citrix. Unfortunately, there was no registry option or any other option available to exclude SUA processes and hence this driver needs to be removed.
With this the SUA works and users can launch C shell. Run the clear command from Korn shell. The steps discussed are based out of testing and alternate workaround.
Support for SFU 3.5 over Windows 2003
There are many customer who are still using Service for Unix ( SFU 3.5) in their environment and looking forward for support from Microsoft on issues which they are facing. Windows 2003 and SFU 3.5 are already out of mainstream support.
https://support.microsoft.com/lifecycle/?p1=3207 ==> Lifecycle support for SFU 3.5
Below link talks about the lifecycle support for Windows 2003:
https://support.microsoft.com/lifecycle/?LN=en-us&p1=3198&x=7&y=13
SFU 3.5 installed over Windows 2003 R2 is unsupported and not recommended. Starting with Windows Server 2003 R2, NFS services were integrated into the operating system.
Tips on 'mount options" on NFS version 4.1
Inputs on NFS 4.1 mount:
While working on a recent scenario on NFS V4.1, we came across some intresting scenarios for mounting the NFS volumes on the Unix NFS clients.
In the implementation of V4.1, there are no particular access requirements to virtual directories , but all relative objects have the relevant security checks applied, namely checks using a combination of the object permissions and the share permissions. In this case, the root directory, namely "/" is virtual and testnfs (i.e. "c:\testnfs") is a real object and so has normal access rules supplied.
This means that you can happily read the directory rooted at "/" as UID 0 with no particular requirements. Hence, the LOOKUP of "testnfs" relative to "/" succeeds.
Analysis from Netmon traces:
From the entmon analysis we found that a attempt is made to issue a GETATTR against the "<NFS-share>" directory as UID 0 from the Unix NFS client. Unlike V2/V3 where GETATTR has no access requirements, V4.1 *does* require that the server verify that the requestor be checked for access for a GETATTR request. So the server will attempt to locate a Windows account matching UID 0. As there is no such mapping, it will attempt to use the Anonymous account, but since anonymous access has been disabled on the share, the attempt will be failed.
Following are the options to mount the NFS share:
- Create a mapping for UID 0 to a Windows account. Note this Windows account does not necessarily have to be a privileged account if it is not being used to apply the special "root" like operations. B
- Allow anonymous access and ensure that the permissions on the objects to be accessed in this way (possibly just the directories being "mounted") allow access via the account being used for anonymous. However in this scenario we need to add anonymous logon in the NTFS permission.
- In case, we do not want to map the root user (UID 0) to an AD user, then we have these options:
- Enable the option "Unmapped Unix user access"
- Or else mount the root ("/" directory) on the Unix NFS clients.
- Check "Allow anonymous access". However this will not work unless we add the anonymous logon in the NTFS permission.
- This is something I have not tried but can be done from the Unix side. Issue the UNIX mount in the context of the account needing access. That is, allow the UNIX user to mount the target share themselves to somewhere in their own local namespace.
Unable to access Symbolic link on a NFS share
While working on one of the case, the customer reported that he was unable to access symbolic link of a NFS share. The symbolic link was pointing to another directory under the same NFS share. The NFS share was hosted on Windows 2008 R2. While checking the properties of the link, we found that the link was created using the UNC path instead of the absolute path. We suggested the customer to create another symbolic link and in the target field put the absolute path of the directory.
For example, refer to the command below. Both the command completes with a success and the link is created for each of the command.
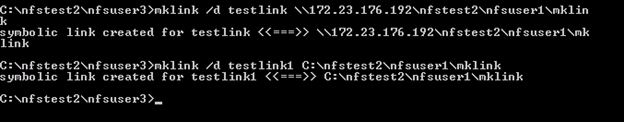
We mounted the share on the Link machine and then ran the ls –l command to check the attributes\permission of the files and folder. As highlighted below, for testlink (which was created using UNC path) the Linux NFS client was unable to pull any information.
But for testlink1 (which was created using absolute path), the Linux NFS client was able to pull the information. Also we got a permission denied while trying to access testlink, but were able to access testlink1.
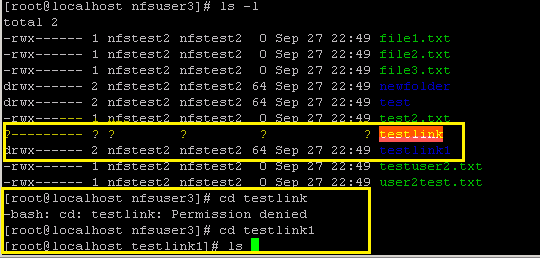
Later we also create a symblolic link ( using mklin) to a target ourside the NFS share and was able to access it from the Linux client. The test which we did had a wide open permission on the NFS share.
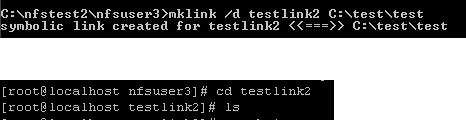
Refer the article https://technet.microsoft.com/en-us/library/cc753194(v=WS.10).aspx to know more about mklink.
Unable to do a RSH from Windows to Unix using domain account
Recently we got a case where customer was unable to run RSH command from Windows RSH client to an AIX RSH server. The error message was "Permission denied".
For RSH client, there is not much of setting that needs to be done on the Windows side. SUA SDK was installed. Also checked the inetd.conf file and removed the comment entries for the following files:
shell stream tcp nowait NULL /usr/sbin/in.rshd in.rshd -a
exec stream tcp nowait NULL /usr/sbin/in.rexecd in.rexecd
login stream tcp nowait NULL /usr/sbin/in.rlogind in.rlogind -a
On the AIX side, RSH was configured using the .rhosts file. The setting is similar to what we do when we set RSH on Windows.
Later we found the issue was happening only with domain users and not with local users. So when we ran the command below logged in as domain user, we got permission denied.
- rsh –l <root> <IP address of RSH server> ls ==> ( Permission denied)
Then we checked the entry in the .rhost file on AIX and found that for the domain users; only the user name was mentioned. We modied the entry as below and restarted the inetd services. This resolved the issue.
"domainName+UserName"
Then customer had another question on the configuration needed for firewall. In the current scenario, we had turned off the firewall setting to allow RSH. We suggested the below settings.
- Control Panel ==> Windows Firewall ==> Advance setting ==> Right click on Inbound rules ==> new rules

- You will get the New Inbound rule Wizard
- Select Port ==> select the option Specific local ports==> mention the range "512-1023" ==> click next
- Select the option Allow the connection ==> click next
- Select all the option Domain, private, public ==> click next
- Givethe rule name and click Finish
- Once done, select the new rule and go to the properties
- click on the tab which says Programs and Services
- Select the option "This program" ( not ALL programs) and browse to the file called psxss.exe under System32 folder.

- By selecting the above option only programs that are being used by psxss.exe would be able to connect on the port.
- There are other options also to make it secure like putting in the computer name.
Unable to do PCNFS on windows 2008 R2"
Recently we got a case where customer was trying to set up Server for PCNFS on Windows 2008 R2. They were moving from Windows 2003, SFU 3.5 to Windows 2008 R2.
Server for PCNFS is no more in Windows 2008. Starting Windows 2003 R2, it was removed. The TechNet article below talks about the same thing.
https://technet.microsoft.com/en-us/library/cc753302%28WS.10%29.aspx
But we can achieve similar functionality using the below options:
1. User Name Mapping server: If you have an existing Windows 2003 / Windows 2003 R2 system; it can still host the User Name Mapping Service. Your Windows 2008 can fetch maps from the system running user name mapping service on Windows 2003 / Windows 2003 R2 system. The only (and most important!) change needed on the system running user name mapping
service is that the .maphosts file (in C:\WINDOWS\msnfs in case on Windows 2003 R2) needs to have a "+" / list of Windows NFS servers so that they can get the maps.
2. Active directory lookup: Windows NFS server can be pointed to fetch the maps directly from Active Directory. The changes which are needed on the Windows Active directory are to populate the UNIX related attributes (below) for related groups and users.
- On the NFS server, we need to put the netbios name of the domain under the ADlookup setting.
- Then we need to populate the following entries on the AD for user's and group
List of attributes for a group:
- gidNumber – an unique number for the group in a domain
List of attributes for a user: (one inbold are mandatory)
- uid –generally the sAMAccountName
- uidNumber – an unique number for the user in a domain
- gidNumber – number same as of the gidNumber of the group to which this user belongs
- msSFU30Name- generally the sAMAccountName
- unixHomeDirectory– home directory for UNIX environment
- loginShell –default shell for user
https://blogs.technet.com/b/sfu/archive/2010/12/09/important-tips-on-nfs-part-1.aspx
3. ADLDS: This is used for the scenario for mapping local users and group in "non-active directory" environment.
Unable to Install SUA SDK on Windows 2008 R2
Recently we got a case where customer reported that he was unable to install the SUA SDk component on Windows 2008 R2.
Customers had added the feature "SubSystem for UNIX-based Applications" and then click on the link as displayed on the image below.
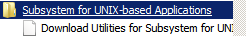
But this opens the Web page for the download utility for Windows 2008 and not Windows 2008 R2. Hence the customer downloaded the SUA SDK tool from incorrect location as below: https://www.microsoft.com/download/en/details.aspx?displaylang=en&id=23754
Suggested the customer to download the utility from the correct URL : https://www.microsoft.com/download/en/details.aspx?displaylang=en&id=2391
After downloading the tool, we were able to install the SUA SDK on Windows 2008 R2.
Unable to run the 'PAX" command in Windows 7, SUA with a '–q' option
Recently we got an case where the customer was looking for assistance to run PAX command in Windows 7 SUA. Unlike SFU 3.5, the PAX command in windows 7, SUA does not have "-q" option to suppress error message. Hence it was failing.
From the man pages we found that using the new parameter "-Q"; the same functionality can be achieved. Though the same may not have been documented on the SUA help files.
Running the man page give the below information:
-Q Quiet warnings about files being archived without additional ACL
Quiet messages that will not affect the success of the installation. This is usually used to quiet (supress) messages that may appear to the average user to be indicating a problem when there really is no problem. This does not conflict with the -v option.
More on PAX could be found on the URL https://en.wikipedia.org/wiki/Pax_(Unix)
Unable to start "Server for NIS" service; "An error occurred accessing the Windows Registry. Error: %1"
Recently we go an issue where the "Server for NIS" service was not starting on Windows 2003 R2, x64.
The error code as per the vent logs was: Event ID 8194. We referred to the TechNet document https://technet.microsoft.com/en-us/library/dd316252(v=ws.10).aspx and followed the instruction. But this did not help.
We also checked the schema on the DC and it looks good. Even the registry entries for "server for NFS" were correct. With further troubleshooting found that the size for the Nissvc.exe was incorrect. The file size was for x86 bit O/S and not x64. Informed the customer that nissvc.exe has been installed from incorrect media (x86) on x64 bit O/S.
Customer uninstalled the Server for NIS and then reinstalled it using the correct media. This resolved the issue. Another way to resolve the issue was to update the NIS drivers from the KB https://support.microsoft.com/kb/969839 as this would replace the nissve.exe, x86 bit file with nissve.exe, x64 bit.
Unix Attribute Tab does not show all the UNIX provisioned groups in Primary Group Name ==>GID drop down.
While working on a issue recently, we found that the Unix attribute tab has a GUI limitation on the number of groups it can display.
Customer came with an issue where they had provisioned about 1500 groups but from ADUC ==> User's properties ==> Unix attribute tab, all the groups were not listed. For example refer the image below:
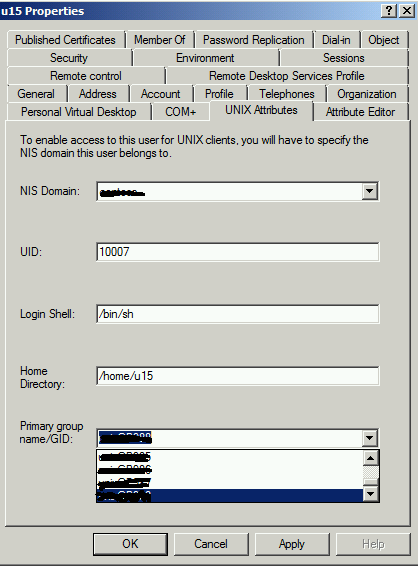
Based on our research we found that the GUI is designed to show 1000 groups by default. Nisprop.dll makes LDAP calls to the Active Directory to query groups which are provisioned for Unix.
One of the work around for the issue given to the customer was to add the gidNumber of the group which are not displayed through the Unix attribute tab.
The same can be achieved from Windows 2008 R2 DC, through the attribute editor tab.
Solution:
But the questions still remains that, if there is another option to manage the number for group displayed through the Unix attribute tab.
You can increase the MaxPageSize(which is by default 1000). Changing value over 1000 to something as applicable will do the trick. However, there may cause some performance issues. So, please try it out in your test environment first.
Steps: (To be performed on a Domain controller)
1) From the command line, type NTDSUTIL and press enter.
2) At the NTDSUTIL: prompt, type LDAP Policies and press enter.
3) At the LDAP Policy: prompt, type Connections and press enter.
4) At the Connections: prompt, type Connect to Server <domain controller name> and press enter.
5) At the Connections: prompt, type Quit and press enter.
6) At the LDAP Policy: prompt, type Set MaxPageSize to <number, eg. 1500 > and press enter.
7) At the LDAP Policy: prompt, type Commit Changes and press enter.
8) At the LDAP Policy: prompt, type Quit and press enter.
9) At the NTDSUTIL: prompt, type Quit and press enter.
This will list the additional groups through ADUC .
WSRM configuration: SUA does not work properly on Multi Processor machines
Recently we got multiple issues where the SUA performance was getting impacted on multi-processor machines. While the issue is still being diagnosed for the root cause, we were able to get a workaround around this.
Some of the common issues were:
1. Slow performance
2. Long running commands fails
3. SUA crashing Intermittently
There was a hotfix https://support.microsoft.com/kb/2639164 released for SUA performance running GPFS with SUA. But this did not address all race conditions that may appear. To eliminate the race condition, we can try the WSRM option. This would be just a recommendation and may or may not work on all scenarios. The workaround recommended was to configure WSRM so that subsystem (psxss.exe) uses only one CPU.
Steps to configure WSRM:
1. Installation: Adding feature
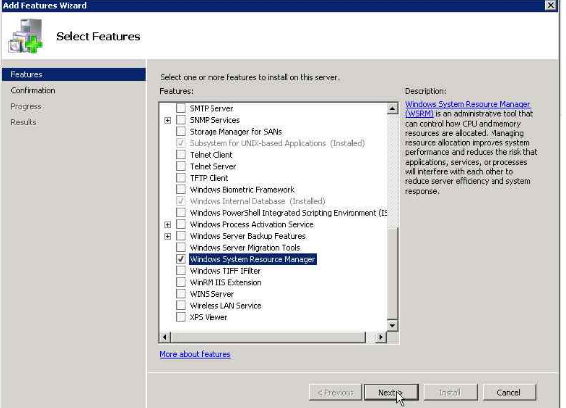
2. Step 1 will need reboot. Once done, open WSRM
3. Steps to configure WSRM
4. Adding a New resource Allocation policy
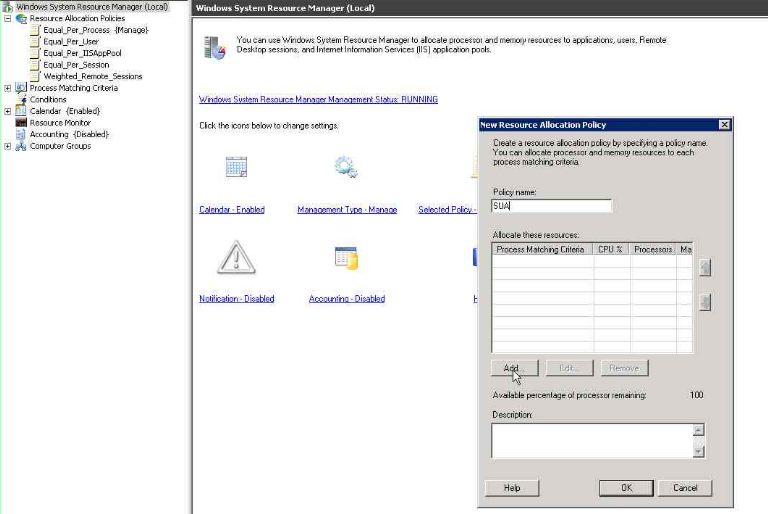
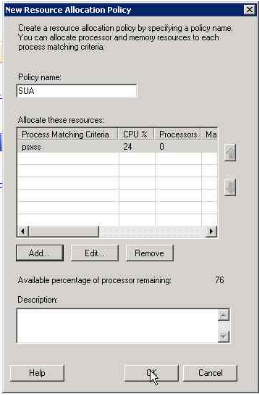
5. Giving the policy name
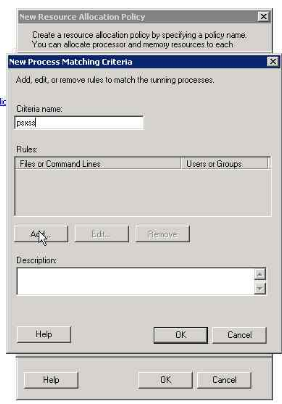
6. Selecting a new process matching criteria
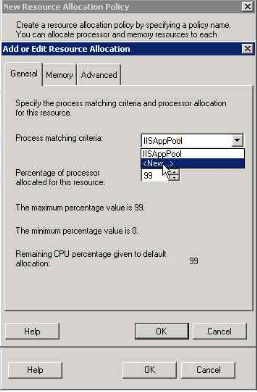
7. Gving the criteria name
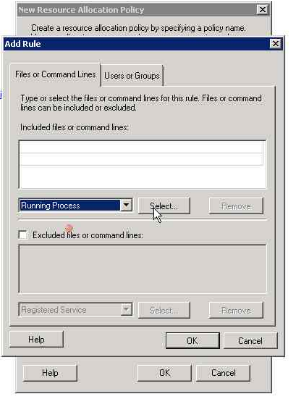
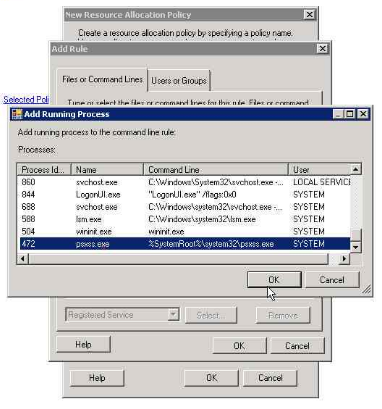
8. selecting the running process (psxss.exe in this case)
9. Details
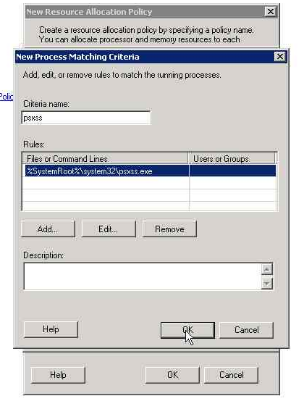
10. Selecting the resource allocation (0 in this case as we want SUA to only use 1 CPU)
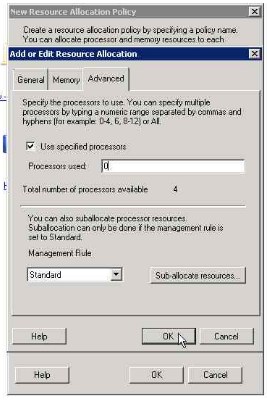
11. You will get the message below
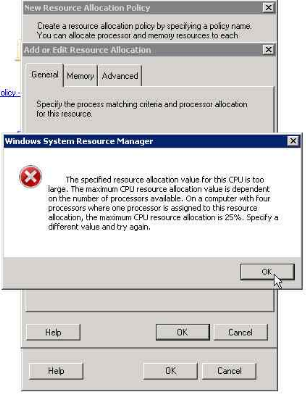
12. selecting the percentage of resource allocated (24 in this case as we have total 4 processor and have opted to use only 1 for SUA)
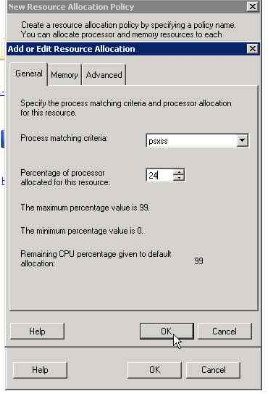
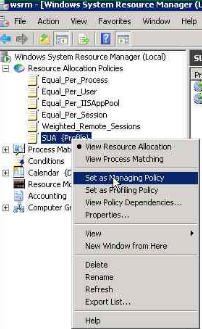
13. Now we need to right click on the profile and mark it as "Set as Managing policy"
14. To verify the same from task manager (check the processor affinity)
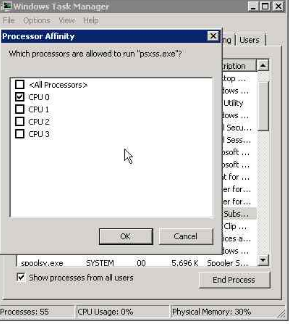
Once done, please monitor the SUA performance.
Ad Blocker for IE 8
According to a friend of mine here at MS, there isn't a really good ad blocker for IE8 yet so he wrote his own at https://adblockie.codeplex.com/.
Anime at Microsoft
Microsoft has a lot of internal mailing lists. Any full time employee could create their own mailing list and add members. Conversely, any 'softie could apply to join a mailing list as well. One of these mailing lists at Microsoft is the anime mailing list. Of course you have your more technical mailing list like the F# mailing list. You can ask questions and discuss your favorite animes or F# keyword:)
Anonymous DCOM Problems with remote Hyper V Manager(Access Denied. Unable to Establish Communication)
If you ever run into problems using the remote Hyper V Manager, there is a wonderful little vbscript(hvremote) written by John Howard at https://blogs.technet.com/jhoward/ and https://code.msdn.microsoft.com/HVRemote. You can run it to troubleshot any problems you might encounter when trying to remotely administrate your hyper v servers.
It works well in most situations except when you get an error message that says "Access Denied. Unable to Establish Communication ..." When you run hvremote script /show /target:server, the script will go through a serious of diagnosis steps. Chances are, by default, you do not have anonymous remote dcom access enabled. If that is true, and your hyper v server runs in Windows 2008 instead of Windows 2008 R2, then you will not be able to use hyper v manager remotely. This is due to the fact that the regular windows 2008 do not use machine credentials when calling fallback methods.
When I first encountered this problem, I thought it was wierd because I could still use wmi remotely to do what I needed my server to do. Then I realized that hyper v manager also uses async calls to manage the server. When the server tries to communicate back via a DCOM call, your client machine rejects it because the server doesn't have the correct credential to communicate with the client. Kinda wierd.
To solve this problem, we can either enable anonymous DCOM access, which is a security breach. You can decide on whether you want to do that. Or we could upgrade our server to Windows 2008 R2. Personally, I don't know what's involved for a third party to do that. Fortunately, within Microsoft, it's pretty easy to upgrade a machine's OS.
Popular posts from this blog
[Excel] 문서에 오류가 있는지 확인하는 방법 Excel 문서를 편집하는 도중에 "셀 서식이 너무 많습니다." 메시지가 나오면서 서식을 더 이상 추가할 수 없거나, 문서의 크기가 예상보다 너무 클 때 , 특정 이름이 이미 있다는 메시지가 나오면서 '이름 충돌' 메시지가 계속 나올 때 가 있을 것입니다. 문서에 오류가 있는지 확인하는 방법에 대해서 설명합니다. ※ 문서를 수정하기 전에 수정 과정에서 데이터가 손실될 가능성이 있으므로 백업 본을 하나 만들어 놓습니다. 현상 및 원인 "셀 서식이 너무 많습니다." Excel의 Workbook은 97-2003 버전의 경우 약 4,000개 2007 버전의 경우 약 64,000개 의 서로 다른 셀 서식 조합을 가질 수 있습니다. 셀 서식 조합이라는 것은 글꼴 서식(예- 글꼴 종류, 크기, 기울임, 굵은 글꼴, 밑줄 등)이나 괘선(괘선의 위치, 색상 등), 무늬나 음영, 표시 형식, 맞춤, 셀 보호 등 을 포함합니다. Excel 2007에서는 1,024개의 전역 글꼴 종류를 사용할 수 있고 통합 문서당 512개까지 사용할 수 있습니다. 따라서 셀 서식 조합의 개수 제한을 초과한 경우에는 "셀 서식이 너무 많습니다." 메시지가 발생하는 것입니다. 그러나 대부분의 경우, 사용자가 직접 넣은 서식으로 개수 제한을 초과하는 경우는 드뭅니다. 셀 서식이 개수 제한을 넘도록 자동으로 서식을 추가해 주는 Laroux나 Pldt 같은 매크로 바이러스 에 감염이 되었거나, 매크로 바이러스에 감염이 되었던 문서의 시트를 [시트 이동/복사]하여 가져온 경우 시트의 서식, 스타일이 옮겨와 문제가 될 수 있습니다. "셀 서식이 너무 많습니다." 메시지가 발생하지 않도록 하기 위한 예방법 글꼴(종류, 크기, 색, 굵기, 기울임, 밑줄), 셀 채우기 색, 행 높이, 열 너비, 테두리(선 종류, ...
ASP.NET AJAX RC 1 is here! Download now
Moving on with WebParticles 1 Deploying to the _app_bin folder This post adds to Tony Rabun's post "WebParticles: Developing and Using Web User Controls WebParts in Microsoft Office SharePoint Server 2007" . In the original post, the web part DLLs are deployed in the GAC. During the development period, this could become a bit of a pain as you will be doing numerous compile, deploy then test cycles. Putting the DLLs in the _app_bin folder of the SharePoint web application makes things a bit easier. Make sure the web part class that load the user control has the GUID attribute and the constructor sets the export mode to all. Figure 1 - The web part class 2. Add the AllowPartiallyTrustedCallers Attribute to the AssemblyInfo.cs file of the web part project and all other DLL projects it is referencing. Figure 2 - Marking the assembly with AllowPartiallyTrustedCallers attribute 3. Copy all the DLLs from the bin folder of the web part...
Architecture Testing Guide Released
视频教程和截图:Windows8.1 Update 1 [原文发表地址] : Video Tutorial and Screenshots: Windows 8.1 Update 1 [原文发表时间] : 4/3/2014 我有一个私人的MSDN账户,所以我第一时间下载安装了Windows8.1 Update,在未来的几周内他将会慢慢的被公诸于世。 这会是最终的版本吗?它只是一项显著的改进而已。我在用X1碳触摸屏的笔记本电脑,虽然他有一个触摸屏,但我经常用的却是鼠标和键盘。在Store应用程序(全屏)和桌面程序之间来回切换让我感到很惬意,但总是会有一点瑕疵。你正在跨越两个世界。我想要生活在统一的世界,而这个Windows的更新以统一的度量方式将他们二者合并到一起,这就意味着当我使用我的电脑的时候会非常流畅。 我刚刚公开了一个全新的5分钟长YouTube视频,它可以带你参观一下一些新功能。 https://www.youtube.com/watch?feature=player_embedded&v=BcW8wu0Qnew#t=0 在你升级完成之后,你会立刻注意到Windows Store-一个全屏的应用程序,请注意它是固定在你的桌面的任务栏上。现在你也可以把任何的应用程序固定到你的任务栏上。 甚至更好,你可以右键关闭它们,就像以前一样: 像Xbox Music这种使用媒体控件的Windows Store应用程序也能获得类似于任务栏按钮内嵌媒体控件的任务栏功能增强。在这里,当我在桌面的时候,我可以控制Windows Store里面的音乐。当你按音量键的时候,通用音乐的控件也会弹出来。 现在开始界面上会有一个电源按钮和搜索键 如果你用鼠标右键单击一个固定的磁片形图标(或按Shift+F10),你将会看到熟悉的菜单,通过菜单你可以改变大小,固定到任务栏等等。 还添加了一些不错的功能和微妙变化,这对经常出差的我来说非常棒。我现在可以管理我已知的Wi-Fi网络了,这在Win7里面是被去掉了或是隐藏了,以至于我曾经写了一个实用的 管理无线网络程序 。好了,现在它又可用了。 你可以将鼠标移至Windows Store应用程序的顶部,一个小标题栏会出现。单击标题栏的左边,然后你就可以...

























Comments
Post a Comment